As a common topic that needs to be resolved a lot of times I thought it would be good to do a basic write-up of a basic double NAT configuration to resolve overlapping IP ranges over a link.
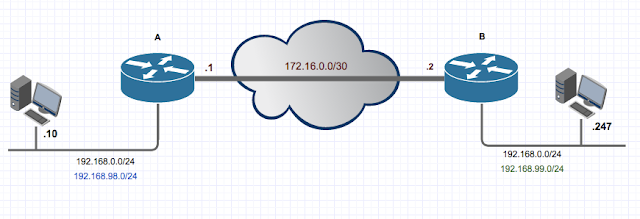
The sample scenario would be as depicted below:
Location A and B with duplicate IP ranges (192.168.0.0/24) on both sides and a VPN link between the two on network 172.16.0.0./30
For this example we would assume two random IP's that needs to be reached from either end, these will be 192.168.0.10 and 192.168.0.247
Router B:
Install a route on router A to route all 192.168.99.0/24 traffic to the gateway address of router B (172.16.0.2)
Netmap is used to ensure there is a 1:1 mapping on the last octet; that way we will know what machine the traffic originated from.
On Router B a route needs to be installed to route the NATed traffic (.98.0/24) back to router A and destination NAT it to the real IP addresses in network B.
/ip route
add dst-address=192.168.98.0/24 gateway=172.16.0.1
And the destination NAT rule to route the traffic to the 192.168.0.247 IP on network B (In this example one rule for each server you want to reach)
add chain=dstnat dst-address=192.168.99.247 action=dst-nat to-address=192.168.0.247
To reach 192.168.0.10 on router A do exactly the opposite, netmap the range to 192.168.99.x on router B and add a destination NAT on router A.
/ip firewall nat
add chain=srcnat src-address=192.168.0.2-192.168.0.254 dst-address=192.168.98.0/24 action=netmap to-addresses=192.168.99.2-192.168.99.254
To further make things easier to use either DNS entries can be used or if the IP addresses you want to route to on the remote subnet are not used locally add them locally with a destination NAT so that you can use the real IP address locally to reach the remote server.
Sample:
The sample scenario would be as depicted below:
Location A and B with duplicate IP ranges (192.168.0.0/24) on both sides and a VPN link between the two on network 172.16.0.0./30
For this example we would assume two random IP's that needs to be reached from either end, these will be 192.168.0.10 and 192.168.0.247
To make the mikrotik commands more descriptive all local networks (LAN A and LAN B) are connected to "ether2" interface and the link between the two routers to the "ether1" interfaces.
Router A:
/ip address
add address=192.168.0.1/24 interface=ether2
add address=172.16.0.1/30 interface=ether1
add address=192.168.0.1/24 interface=ether2
add address=172.16.0.1/30 interface=ether1
Router B:
/ip address
add address=192.168.0.1/24 interface=ether2
add address=172.16.0.2/30 interface=ether1
The next step would be to select two unused/free/unrouted IP ranges in the network that can be used at network A & B, for this example 192.168.98.0/24 and 192.168.99.0/24 were selected.add address=192.168.0.1/24 interface=ether2
add address=172.16.0.2/30 interface=ether1
Install a route on router A to route all 192.168.99.0/24 traffic to the gateway address of router B (172.16.0.2)
Router A:
/ip route
add dst-address=192.168.99.0/24 gateway=172.16.0.2
Then install a source NAT rule that changes the source address of the
packets from network A to 192.168.98.0/24. Packets will now have that changed source
address and be forwarded to router B.add dst-address=192.168.99.0/24 gateway=172.16.0.2
Router A:
/ip firewall nat
add chain=srcnat src-address=192.168.0.2-192.168.0.254 dst-address=192.168.99.0/24 action=netmap to-addresses=192.168.98.2-192.168.98.254
add chain=srcnat src-address=192.168.0.2-192.168.0.254 dst-address=192.168.99.0/24 action=netmap to-addresses=192.168.98.2-192.168.98.254
Netmap is used to ensure there is a 1:1 mapping on the last octet; that way we will know what machine the traffic originated from.
On Router B a route needs to be installed to route the NATed traffic (.98.0/24) back to router A and destination NAT it to the real IP addresses in network B.
Router B:
add dst-address=192.168.98.0/24 gateway=172.16.0.1
And the destination NAT rule to route the traffic to the 192.168.0.247 IP on network B (In this example one rule for each server you want to reach)
Router B:
/ip firewall natadd chain=dstnat dst-address=192.168.99.247 action=dst-nat to-address=192.168.0.247
To reach 192.168.0.10 on router A do exactly the opposite, netmap the range to 192.168.99.x on router B and add a destination NAT on router A.
Router B:
add chain=srcnat src-address=192.168.0.2-192.168.0.254 dst-address=192.168.98.0/24 action=netmap to-addresses=192.168.99.2-192.168.99.254
Router A:
/ip firewall nat
add chain=dstnat dst-address=192.168.98.10 action=dst-nat to-address=192.168.0.10
This should complete the setup and you should be able to ping 192.168.99.247 from an IP on router A LAN subnet.add chain=dstnat dst-address=192.168.98.10 action=dst-nat to-address=192.168.0.10
To further make things easier to use either DNS entries can be used or if the IP addresses you want to route to on the remote subnet are not used locally add them locally with a destination NAT so that you can use the real IP address locally to reach the remote server.
Sample:
Router A:
/ip firewall nat
add chain=dstnat in-interface=ether2 dst-address=192.168.0.247 action=dst-nat to-address=192.168.99.247
add chain=dstnat in-interface=ether2 dst-address=192.168.0.247 action=dst-nat to-address=192.168.99.247

Por qué estás haciendo un NAT de los Host específicos? si ya hiciste un netmap generando un NAT para toda la subnet. Es realmente necesario? Que sentido tiene entonces el netmap?
ReplyDeleteThis And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download Now
Delete>>>>> Download Full
This And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download LINK
>>>>> Download Now
This And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download Full
>>>>> Download LINK 0V
The last DST-NAT is an further example of how it can be done.
ReplyDeletehow to change this scenario to cover whole subnet in each side instead of adding them one by one
ReplyDeleteThanks for sharing the info, keep up the good work going.... I really enjoyed exploring your site. good resource...
ReplyDeletehide my ass reviews
This And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download Now
ReplyDelete>>>>> Download Full
This And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download LINK
>>>>> Download Now
This And That: Mikrotik Overlapping Ip Subnets On Vpn Link >>>>> Download Full
>>>>> Download LINK lz